Many organizations lack the visibility of their resources in the cloud, which can cause misconfigurations to go unnoticed for a longer period. This can make applications vulnerable. For example, organizations are unaware of how many cloud resources they are running and how they are all configured.
Gartner reports that by 2025 (https://www.gartner.com/smarterwithgartner/is-the-cloud-secure), the following will apply:
- 90% of organizations will inappropriately expose their sensitive data if they fail to control public cloud use
- 99% of cloud security failures will be the fault of cloud customers
Threat landscape refers to the evolving and dynamic state of security threats and vulnerabilities, including the types of threats, their sources, and the ways they can be carried out. The threat landscape changes frequently, and organizations need to continuously monitor and update their security measures to stay ahead of the latest threats.
In the cloud, the threat landscape includes a wide range of risks, such as unauthorized access to data, misconfigured cloud services, and compromised cloud accounts. CSPM helps organizations to stay on top of these threats by providing continuous visibility and control over their cloud security posture, allowing them to detect, respond to, and mitigate security risks in real time.
Security breaches are growing every year and regulatory compliance policies are becoming more stringent day by day. Thus, many security breaches carry huge monetary consequences, but more than that, they bring reputational damage as well.
Figure 2.2 is from Statista, and it describes the average cost of data breaches in the United States between 2006 and 2022. Let us take a close look:
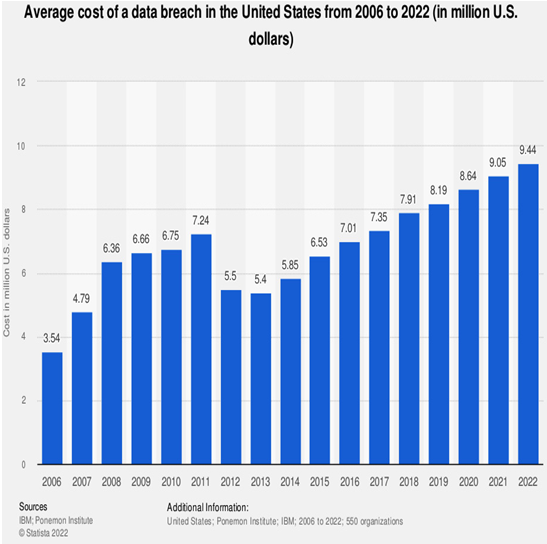
Figure 2.2 – Average cost of data breaches (source: https://www.statista.com/statistics/273575/us-average-cost-incurred-by-a-data-breach/)
With these trends, predictions, and day-to-day headlines, it is evident that organizations need to be more attentive toward their security posture. This is where CSPM comes into the picture to bridge the gap. Let us explore some of the reasons CSPM is important:
- Compliance benchmarks: Compliance benchmarks are sets of guidelines or best practices that are designed to help organizations achieve a specific level of security. Compliance benchmarks are often created by organizations such as the Center for Internet Security (CIS) and are intended to help organizations meet specific compliance requirements or address specific security risks. CSPM solutions can help organizations achieve compliance with compliance benchmarks by providing visibility into their cloud environment and identifying security misconfigurations and vulnerabilities that could lead to compliance violations. CSPM solutions can also automate the assessment process, reducing the manual effort required to ensure compliance.
- Security standards: Compliance benchmarks and security standards are related but distinct concepts. Security standards are typically more broadly defined and apply to a wide range of organizations and industries. Examples of security standards include ISO/IEC 27001, the Payment Card Industry Data Security Standard (PCI DSS), and the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Security standards provide a framework for organizations to establish, implement, maintain, and continually improve their security management systems. CSPM solutions help organizations achieve compliance with security standards by providing continuous visibility into their cloud environment and identifying security misconfigurations and vulnerabilities that could lead to security breaches or compliance violations. Most CSPM solutions also automate the assessment process, reducing the manual effort required to ensure compliance with security standards.
- Protects sensitive data: With the increasing use of cloud services, it is important to ensure that sensitive data is protected from cyber threats such as data breaches, hacking, and unauthorized access. CSPM helps organizations secure their data in the cloud by monitoring the environment for vulnerabilities and implementing security controls.
- Identifies risks: CSPM helps organizations identify potential risks in their cloud environment, such as misconfigured security settings, outdated software, and unpatched vulnerabilities, so that they can take steps to mitigate these risks before they become a threat.
- Improves visibility: CSPM provides organizations with visibility into their cloud security posture, allowing them to understand what resources are in place and what changes need to be made to ensure that the environment is secure.
- Continuous monitoring: CSPM continuously monitors the cloud environment, which enables organizations to detect and respond to security incidents in real time, reducing the risk of damage to the environment and the business.
Overall, CSPM is important because it helps organizations secure their cloud environment, maintain compliance with regulations, and protect sensitive data. By implementing a robust CSPM program, organizations can enhance their security posture, protect their critical assets, and reduce the risk of data breaches and other security incidents in the cloud. Let us take a look at the key capabilities and core components of CSPM tools.
